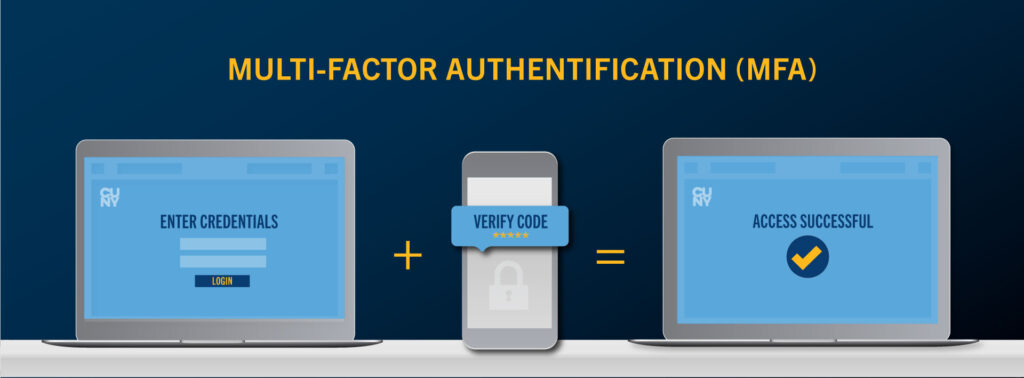
Multi-Factor Authentication (MFA)
Why MFA?
MFA is standard practice at most colleges, universities, and businesses when those businesses provide access to protected information. It helps protect personal and institutional information from theft, cyberattack, and ransomware. MFA protects your account and Trinity College because when you sign in, you prove your identity in two ways: with something you know (a password) and something you have (usually a phone). Additionally, Trinity College must use MFA to comply with insurance and compliance requirements. Trinity College requires MFA for all community members. We are using MFA for all Office 365 apps (like email, Teams, W ord, etc.). Please visit What is: Microsoft Multifactor Authentication to learn more.
MFA Implementation & Set-Up
MFA Setup:
- Go to https://aka.ms/MFAsetup and sign in with your username, like [email protected]
- You’ll be walked through downloading the Microsoft Authenticator app.
- Tip: After downloading the app, open it, but immediately return to your browser (trying to sign in from inside the app gets confusing).
- Once finished, we recommend returning to https://aka.ms/MFAsetup to add a phone as a backup sign-in method. Here’s a video on managing second factors.
- Please see the Microsoft MFA Setup Page or Video Walkthrough for additional assistance.
Enable Passwordless phone sign-in:
- In the Microsoft Authenticator app, select the account registered.
- Select Enable phone sign-in.
- Follow the instructions in the app to finish registering the account for Passwordless phone sign-in.
For further guidance from Microsoft, click here. Additionally, here is a Video Walkthrough: Authenticator App Registration
Additional Notes
- Frequency of Authentication – You will need to authenticate with MFA every 30 days or when there is unusual activity detected by Microsoft.
- Computer Rebooting – When you reboot your computer, it doesn’t log you out of the desktop applications. Hence, you cannot expect a reboot to trigger a Multi-factor Authentication prompt.
- Tablets – It may be convenient to have the Microsoft Authenticator app for iOS or the Microsoft Authenticator app for Android on your tablet in addition to your phone. If you do so, you can use your tablet to authenticate in case you get a new phone or new phone number.
- Microsoft Authenticator per Device – You only need to download the Microsoft Authenticator app on one device to be able to authenticate logins. For instance, when you log into Teams on a laptop, you can confirm the login with the Microsoft Authenticator app on your mobile phone.
- Tip: It’s smart to add the Microsoft Authenticator app to a second device, in case you have problems with your main device.
MFA Troubleshooting and Tips
Tip: Going where you don’t have signal or data…
We suggest you download and configure the Microsoft Authenticator app before you leave. With it, you can sign in without receiving a text message. If your phone is connected to the Internet, you can approve sign-ins via notifications. If your phone is not connected to the Internet, the Microsoft Authenticator app can still generate codes that you can use for authentication.
Tip (Employees): I left my mobile phone at home, and I’m at work…
Have MFA trouble? This Multi-Factor Authentication (MFA) reset form should be used if you are having trouble gaining access to your account via your current MFA methods. Possible scenarios where this could happen include:
- You’ve received a new phone number which is no longer connected to your account.
- A new smart device has prevented your Authenticator application from working properly.
- You aren’t receiving authentication notifications properly.
If we are able to verify your identity against our records, your passwords will be reset within two business days.
After a reset, your next log-on will require a new Multi-Factor Authentication method before accessing your account.
Please contact the Help Desk [email protected], 860.297.2100, or visit us on Level A of the Raether Library and Information Technology Center during scheduled hours for additional questions.
What are the Trinity-approved Multifactor Authentication Methods?
Microsoft Multifactor Authentication Application
Use Microsoft Authenticator for easy, secure sign-ins for all your online accounts using multi-factor authentication. For an even easier login experience, enable “Phone Sign-In.” Once enabled, you should be able to use passwordless sign-in to access your account. When signing in, you will be shown a number. Open the Authenticator app and type in or select the correct number. After putting in the number, you will have to use Face ID or fingerprint authentication, depending on your device.
FIDO2 security key
One of the most popular FIDO2 security keys is YubiKey. YubiKey is a USB stick that you can plug in and be set up to use as an authentication method. The YubiKey can be used as a last resort option in case you lose or do not have access to your phone or other means of verification. The user can complete a setup within the Manage “Second Factors” within their Microsoft Account.
OATH hardware token
One of the most popular and recommended OATH hardware tokens is Protectimus. It comes in the form of a keyfob making it more durable and reliable. Please contact the Library and Information Technology Services division to set up your hardware token. Self-setup is not permitted.
Voice Call (Wireless or Landline)
With phone call verification during SSPR or Azure AD Multi-Factor Authentication, an automated voice call is made to the phone number registered by the user. The user is prompted to press # on their keypad to complete the sign-in process. TIP: If you lose or do not have access to your other authentication methods, you can add a landline such as your home phone or office number. You can set it up so that your emergency contact will get a call to authenticate your login. Ensure that they know they MUST contact you before they approve any access to your account.